In Windows 7, make sure you open Command Prompt under Administrative mode.
On Server machine:
$ keytool -genkey -alias SrvKeystore -keypass abcd123 -keystore SrvKeystore -storepass abcd123
What is your first and last name?
[Unknown]: G P
What is the name of your organizational unit?
[Unknown]: GauZ
What is the name of your organization?
[Unknown]: GauZ
What is the name of your City or Locality?
[Unknown]: NYC
What is the name of your State or Province?
[Unknown]: NY
What is the two-letter country code for this unit?
[Unknown]: US
Is CN=G P, OU=GauZ, O=GauZ, L=NYC, ST=NY, C=US correct?
[no]: yes
On Client machine:
$ keytool -genkey -alias CliKeystore -keypass abcd123 -keystore CliKeystore -storepass abcd123
What is your first and last name?
[Unknown]: P G
What is the name of your organizational unit?
[Unknown]: ZuaG
What is the name of your organization?
[Unknown]: ZuaG
What is the name of your City or Locality?
[Unknown]: NYV
What is the name of your State or Province?
[Unknown]: NY
What is the two-letter country code for this unit?
[Unknown]: US
Is CN=P G, OU=ZuaG, O=ZuaG, L=NYV, ST=NY, C=US correct?
[no]: yes
$ keytool -export -alias CliKeystore -keystore CliKeystore -file CliCert.cer
Enter keystore password:
Certificate stored in file <CliCert.cer>
Copy CliCert.cer to server machine
On Server machine:
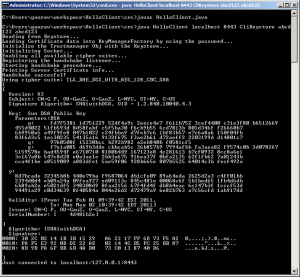
$ keytool -import -alias CliCert -file CliCert.cer -keystore SrvKeystore -keypass abcd123 -storepass abcd123
Owner: CN=P G, OU=ZuaG, O=ZuaG, L=NYV, ST=NY, C=US
Issuer: CN=P G, OU=ZuaG, O=ZuaG, L=NYV, ST=NY, C=US
Serial number: 4d481b66
Valid from: Tue Feb 01 09:40:38 EST 2011 until: Mon May 02 10:40:38 EDT 2011
Certificate fingerprints:
MD5: 19:35:1E:1C:39:BC:A4:DA:9C:86:1A:67:6B:0C:4D:86
SHA1: 93:F5:BA:4D:48:02:A1:BE:F1:93:A0:6C:AF:48:AB:84:05:1B:B2:D7
Signature algorithm name: SHA1withDSA
Version: 3
Trust this certificate? [no]: yes
Certificate was added to keystore
$ keytool -export -alias SrvKeystore -keystore SrvKeystore -file SrvCert.cer
Enter keystore password:
Certificate stored in file <SrvCert.cer>
Copy SrvCert.cer to client machine
On Client machine:
$ keytool -import -alias SrvCert -file SrvCert.cer -keystore CliKeystore -keypass abcd123 -storepass abcd123
Owner: CN=G P, OU=GauZ, O=GauZ, L=NYC, ST=NY, C=US
Issuer: CN=G P, OU=GauZ, O=GauZ, L=NYC, ST=NY, C=US
Serial number: 4d481b2e
Valid from: Tue Feb 01 09:39:42 EST 2011 until: Mon May 02 10:39:42 EDT
2011
Certificate fingerprints:
MD5: 83:99:66:6F:C4:84:19:A8:C3:1A:A2:53:DC:0D:9F:8E
SHA1: 69:07:35:5E:A4:56:4D:A4:C5:EC:3C:3C:B3:8B:13:20:6C:86:5D:93
Signature algorithm name: SHA1withDSA
Version: 3
Trust this certificate? [no]: yes
Certificate was added to keystore
Client side: CliKeystore and CliCert.cer
Server side: SrvKeystore and SrvCert.cer
References:
http://download.oracle.com/javase/1.3/docs/tooldocs/win32/keytool.html
http://download.oracle.com/javase/1.5.0/docs/tooldocs/windows/keytool.html
https://www.digicert.com/easy-csr/keytool.htm


Login